Automate Pentesting with Rekono
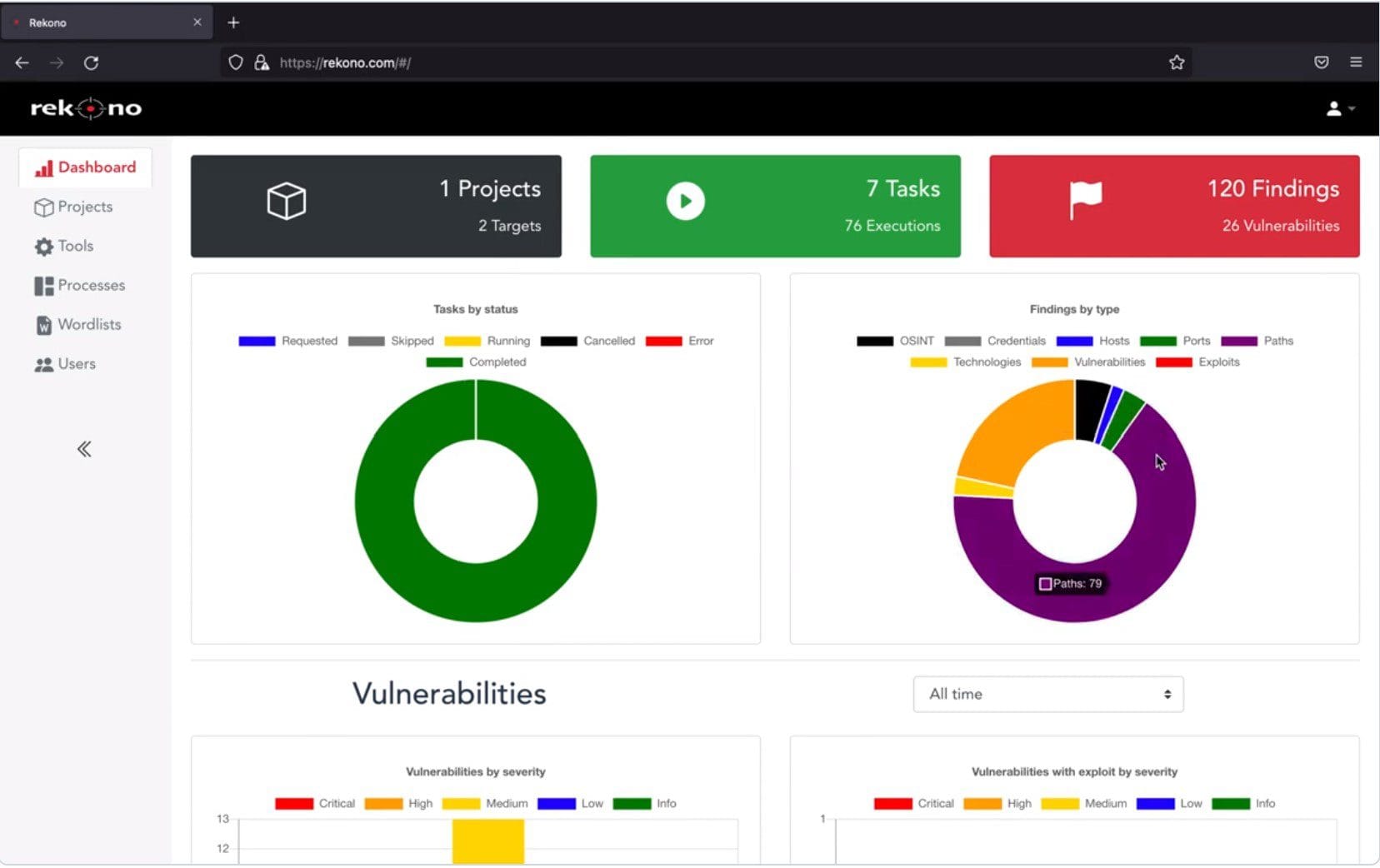
Cybersecurity professionals continually seek efficient tools to identify vulnerabilities before malicious actors exploit them. Rekono is an open-source platform designed for automated penetration testing that simplifies the process while offering a powerful suite of features.
What is Rekono?
Rekono is an automation framework tailored for penetration testing and security assessments. By integrating various tools and scripts into a unified environment, Rekono provides a streamlined, customizable approach to identifying and exploiting security weaknesses. Its intuitive design and modularity make it an excellent choice for both seasoned professionals and newcomers to pentesting.
Key Features of Rekono
- Automation of Repetitive Tasks:
Rekono eliminates the need to perform tedious, repetitive tasks manually. This efficiency allows cybersecurity experts to focus on in-depth analysis and strategic planning. - Tool Integration:
Rekono supports the integration of popular pentesting tools, including Nmap, Metasploit, Burp Suite, and others. This compatibility ensures that users have access to a robust toolkit within a single interface. - Customizability:
With Rekono, users can craft custom workflows tailored to specific assessment needs. This flexibility is ideal for organizations with unique security requirements. - Collaboration Features:
Teams can collaborate seamlessly on pentesting projects, sharing data and insights in real time through Rekono’s platform. - Report Generation:
The platform simplifies the creation of detailed, professional reports—a critical aspect of any pentesting process.
Setting Up Rekono
Getting started with Rekono is straightforward. Here’s a step-by-step guide:
- Configuring Tools:
Integrate your preferred pentesting tools by following the platform’s documentation. Ensure each tool’s dependencies are satisfied. - Creating Workflows:
Use Rekono’s workflow builder to automate tasks. Drag-and-drop components to design a sequence of actions, such as scanning, exploitation, and reporting.
Installation:
Rekono can be installed on Linux systems using Docker. Ensure you have Docker installed, then execute the following commands:
git clone https://github.com/rekono/rekono
cd rekono
docker-compose up
Once installed, access Rekono via your web browser at the specified localhost address.
Practical Use Cases
- Web Application Security Testing:
Rekono can automate vulnerability scanning and exploitation for web applications, identifying issues like SQL injection, XSS, and insecure configurations. - Network Security Assessments:
Conduct network scans with Nmap, followed by automated exploitation using integrated tools, to identify misconfigurations and vulnerabilities. - Compliance Audits:
Rekono’s reporting features make it easier to demonstrate compliance with standards such as PCI DSS, HIPAA, or ISO 27001.
Advantages of Using Rekono
- Efficiency: By automating routine tasks, Rekono significantly reduces the time needed for assessments.
- Accessibility: Its user-friendly interface makes advanced pentesting accessible to a broader audience.
- Community Support: Being open-source, Rekono benefits from an active community of contributors and users.
Challenges and Considerations
While Rekono offers numerous advantages, it’s essential to consider the following:
- Learning Curve: New users might require time to understand and fully utilize Rekono’s capabilities.
- Dependency Management: Proper configuration of integrated tools is crucial to ensure smooth operation.
- Scope Limitations: Rekono’s capabilities are vast but may not cover niche or highly specialized testing needs.
Conclusion
Rekono is revolutionizing the way cybersecurity professionals approach penetration testing. By combining automation, flexibility, and community-driven development, it empowers users to identify and mitigate vulnerabilities effectively. Whether you’re an individual pentester or part of a larger security team, Rekono is a valuable addition to your arsenal.