Using Microsoft Defender’s Attack Surface Reduction (ASR) Rules
Before diving into advanced security solutions like EDR (Endpoint Detection and Response) or XDR (Extended Detection and Response), consider a simpler, yet powerful strategy: reducing the overall attack surface of your endpoints. One often-overlooked solution is Microsoft Defender’s built-in Attack Surface Reduction (ASR) rules. And the best part? These rules come right out of the box and are available for free!
What Are ASR Rules?
Attack Surface Reduction (ASR) rules are specifically designed to block common attack vectors frequently used by cybercriminals. These vectors often target the weakest points in an endpoint’s defenses, such as vulnerable applications and user behavior. By enabling ASR, you can prevent some of the most commonly exploited techniques used by attackers, without needing to install complex security tools or spend additional resources.
Some examples of how ASR rules work include:
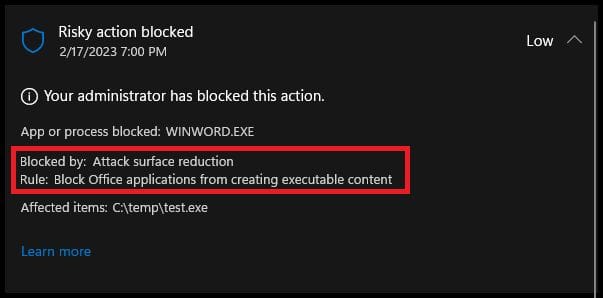
- Blocking Office applications from creating executable content: A common tactic used in malware attacks is to exploit Office files to launch malicious code. ASR helps block this activity, mitigating the risk of such attacks.
- Blocking the execution of potentially obfuscated scripts: Attackers often obfuscate scripts to bypass traditional security measures. With ASR, you can stop these scripts from executing, preventing many common attack types.
- Blocking credential theft from the Windows Local Security Authority Subsystem (lsass.exe): Attackers sometimes try to steal credentials from the lsass.exe process, which is critical for authentication on Windows systems. ASR rules can block this, safeguarding your system from credential-based attacks.
How to Enable ASR Rules
The great news is that enabling ASR rules is straightforward and doesn’t require a dedicated security team or complex setups. You can enable them directly through the Group Policy Editor or with a simple PowerShell command.
Here’s how you can do it:
- Find the Rule GUIDs: Microsoft provides a comprehensive list of ASR rules, each identified by a unique GUID (Globally Unique Identifier). You can access this list in the official Microsoft documentation: https://learn.microsoft.com/en-us/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide
- Enable via Group Policy Editor: If you’re familiar with the Group Policy Editor, you can copy and paste the rule GUIDs into the appropriate configuration to activate them on your endpoints.
- Enable via PowerShell: Alternatively, you can run a PowerShell command to activate the rules programmatically. The PowerShell method is efficient, especially when managing multiple endpoints or implementing bulk changes.
Why Use ASR?
While EDR and XDR tools are important for advanced threat detection and response, ASR rules give you a proactive layer of defense by blocking attacks before they even have a chance to infiltrate your systems. By reducing the attack surface, you’re stopping common threats early, making it harder for cybercriminals to execute their malicious plans.
Plus, since ASR rules are free and built into Microsoft Defender, they’re an easy way to enhance your security posture without additional costs or complex configurations.
Conclusion
In the fight against cyber threats, sometimes the simplest solutions are the most effective. By leveraging Microsoft Defender’s Attack Surface Reduction (ASR) rules, you can reduce the attack surface of your endpoints and proactively block common threats. Before looking into advanced security solutions like EDR and XDR, take the time to enable ASR rules – it’s a quick, easy, and powerful way to make your network more secure.
For more detailed guidance, check out Microsoft’s official documentation and start enhancing your security posture today!