Homelab Security with Security Onion
In the ever-evolving world of cybersecurity, practical experience is invaluable. For enthusiasts and professionals alike, a home lab provides the perfect environment to learn, experiment, and grow. One tool that has gained popularity for home lab security monitoring and intrusion detection is Security Onion. In this blog post, we’ll explore how to deploy Security Onion, leverage its built-in Suricata for network traffic analysis, and take advantage of its pseudo-EDR capabilities to gain a comprehensive understanding of your home network's security posture.
What is Security Onion?
Security Onion is an open-source platform designed for threat hunting, network monitoring, and log management. It combines several powerful tools, including Suricata, Zeek, and the ELK Stack (Elasticsearch, Logstash, and Kibana), into a cohesive and easy-to-use package. While it is widely used in enterprise environments, Security Onion is also perfect for home labs, thanks to its ease of deployment and rich feature set.
Why Use Security Onion in a Home Lab?
- Intrusion Detection System (IDS): With Suricata, Security Onion acts as a powerful IDS, inspecting network traffic for suspicious activities.
- Log Management: The ELK stack provides advanced log aggregation and visualization, making it easier to investigate potential threats.
- Endpoint Monitoring: Security Onion includes tools for endpoint monitoring, giving you pseudo-endpoint Detection and Response (EDR) capabilities.
- Learning Opportunity: By setting up alerts and investigating incidents, you can develop hands-on skills in cybersecurity.
Step-by-Step Deployment
1. Prepare Your Environment
- Hardware Requirements: Ensure you have a machine or virtual environment with at least 4 CPUs, 8GB of RAM, and 250GB of storage. This can scale based on your network size.
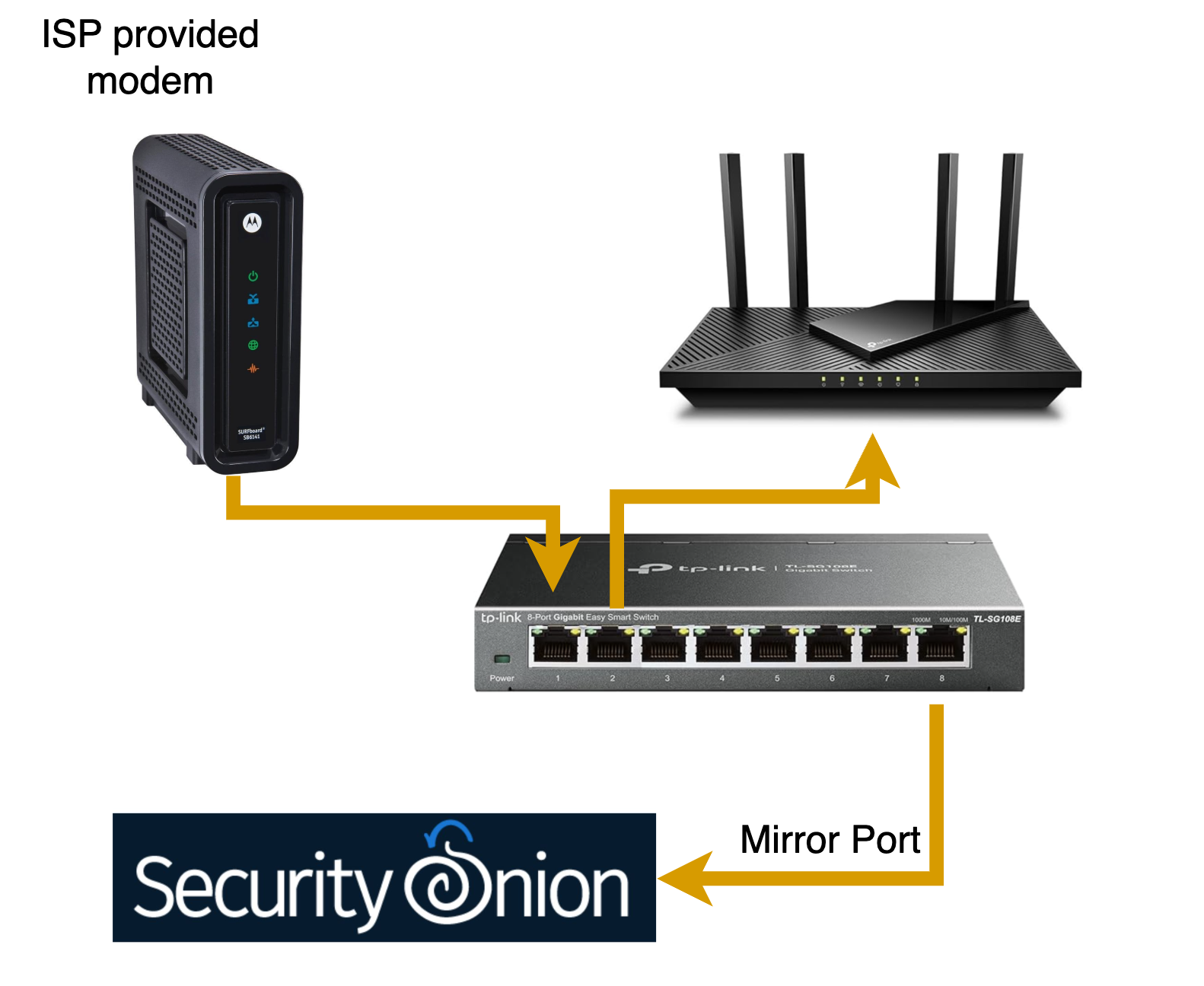
- Network Configuration: You'll need to set up a network tap, SPAN/mirror port, or use a virtualized environment to capture network traffic.
2. Download and Install Security Onion
- Head to the official Security Onion website to download the ISO image.
- Burn the ISO to a USB drive or mount it to a virtual machine for installation.
- Follow the installation prompts, selecting a "Stand-alone" setup for a single system deployment.
3. Set Up Network Monitoring
- After installation, configure a network interface card (NIC) in "promiscuous mode" to capture all network traffic.
- Security Onion will guide you through sensor setup, including choosing data capture tools like Suricata and Zeek.
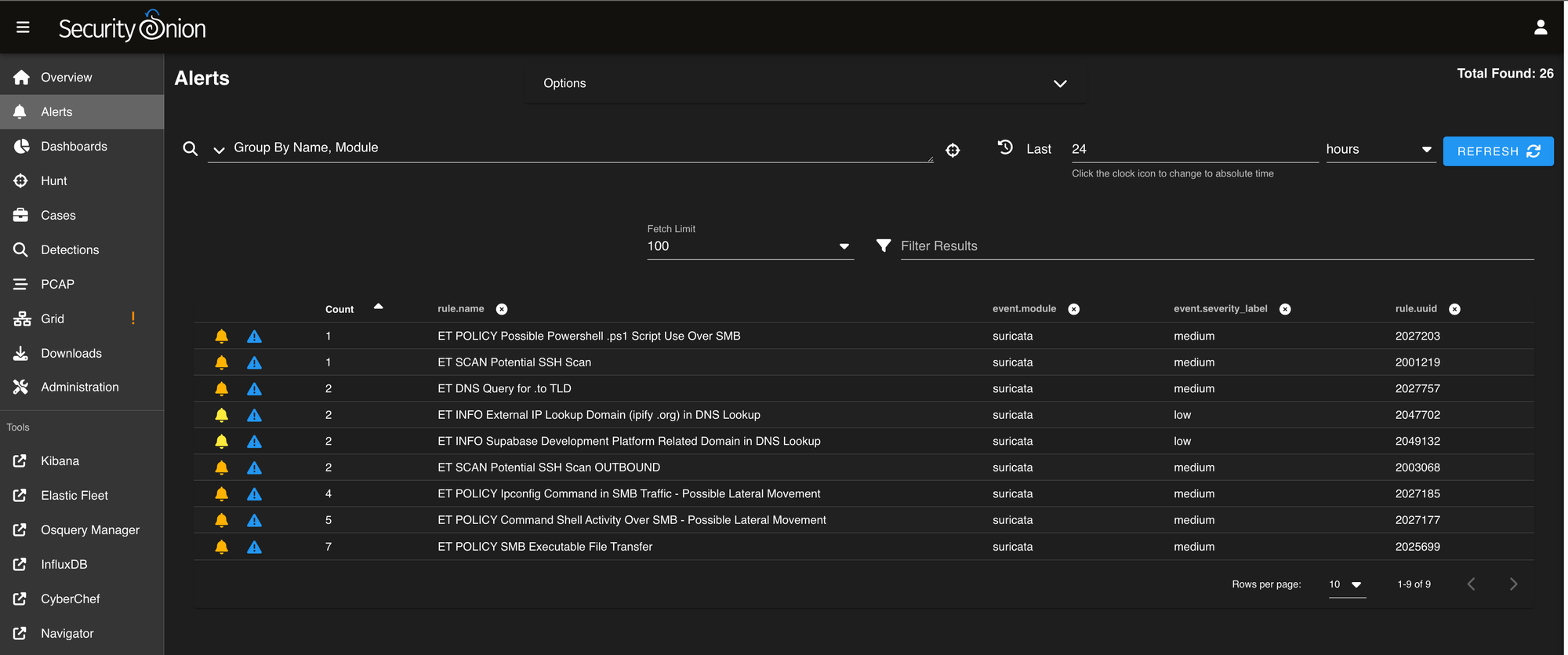
Exploring Pseudo-EDR with Security Onion Agents
Security Onion extends beyond network monitoring by including endpoint monitoring capabilities. By deploying the Elastic Agent or Osquery to endpoints in your lab, you can:
- Collect system logs, process details, and file events.
- Detect suspicious activity, such as unauthorized access or privilege escalation.
- Monitor endpoint health and detect potential malware.
The best part? These features are available in the free version, providing insights that rival entry-level EDR solutions.
Tips for Optimizing Your Setup
- Update Regularly: Keep Security Onion and Suricata signatures up-to-date to stay ahead of emerging threats.
- Tune Alerts: Avoid alert fatigue by tuning out false positives and focusing on meaningful alerts.
- Practice, Practice, Practice: Simulate attacks (e.g., using Kali Linux or Metasploit) to learn how your setup detects and logs malicious activity.
Conclusion
Deploying Security Onion in a home lab is a rewarding way to gain hands-on cybersecurity experience. By combining the powerful network detection capabilities of Suricata with pseudo-EDR functionality and the visualization power of the ELK stack, you can monitor, detect, and investigate threats like a pro.