Forensics with Python - Custom tool for data collection
In the fast-paced world of cybersecurity, responding effectively to incidents is critical. Gathering evidence swiftly and accurately during an incident response is key to mitigating risks and uncovering the root cause. That's where Python Forensics, a new script designed for Windows systems, comes into play. This powerful tool, hosted on my GitHub, provides a streamlined way to collect volatile and non-volatile data from Windows hosts, making it an excellent addition to your incident response toolkit.
https://github.com/xhaabx/WindowsForensics
Why Python Forensics?
When time is of the essence during an incident, having a lightweight, flexible, and reliable tool can make all the difference. Python Forensics is designed to work seamlessly with any Endpoint Detection and Response (EDR) solution, enabling you to quickly gather key forensic artifacts for analysis through live-response.
The script addresses two critical needs:
- Speed and Automation: Automates the collection of various data sources to reduce manual effort.
- Comprehensive Coverage: It retrieves an array of data types, from event logs to current network activity, browser history, and more.
Features and Capabilities
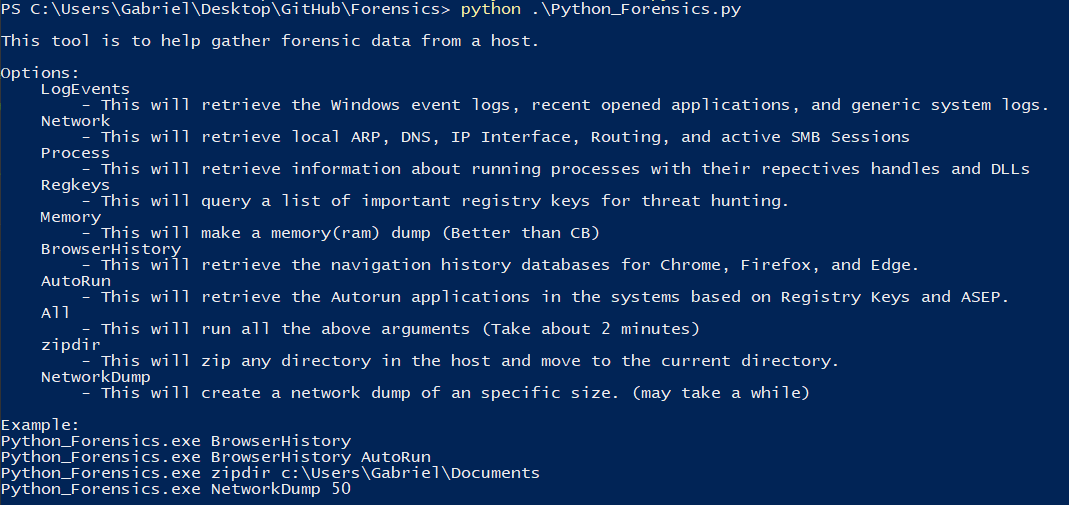
Here’s a breakdown of what Python Forensics can do:
- LogEvents
Retrieves Windows Event Logs, recently opened applications, and system logs for forensic examination. - Network Analysis
Captures local ARP tables, DNS cache, IP configurations, routing tables, and active SMB sessions. - Processes Information
Enumerates running processes along with their respective handles and DLL dependencies. - Registry Keys
Queries critical registry keys to identify potential threats or anomalies. - Memory Dump
Performs a full memory (RAM) dump for in-depth forensic analysis. This feature is optimized for efficiency and provides more actionable insights than some commercial tools. - Browser History
Extracts navigation history for popular browsers like Chrome, Firefox, and Edge. - AutoRun Entries
Identifies AutoRun applications via registry keys and known persistence mechanisms. - All
Execute all the above tasks with a single command, generating a holistic snapshot of the system state. - ZipDir and NetworkDump
- ZipDir: Archives a specified directory for easy data packaging and transfer.
- NetworkDump: Creates a network traffic dump of a specified size for traffic analysis.
How to Use Python Forensics
Using the script is straightforward. After cloning the repository, you can run specific modules or execute the complete suite with the All argument. Here's an example of its usage:
Retrieve browser historypython Python_Forensics.py BrowserHistory
Combine multiple featurespython Python_Forensics.py BrowserHistory AutoRun
Create a network dump of 50MBpython Python_Forensics.py NetworkDump 50
Alternatively, you can also compile it into an executable with autopytoexe.
Real-World Application
This tool is invaluable for incident response teams who need immediate visibility into a compromised system. Whether you're investigating malware infections, unauthorized access, or suspicious activity, Python Forensics helps you:
- Detect persistence mechanisms.
- Trace network connections.
- Analyze memory for malicious processes.
- Uncover browser-based threats or data exfiltration attempts.
Conclusion
Python Forensics is a robust and flexible solution for gathering forensic data from Windows systems. Its versatility, ease of use, and comprehensive functionality make it an essential tool for security professionals and incident responders.