Demystifying a C2 Infrastructure - Breaking Down the Layers
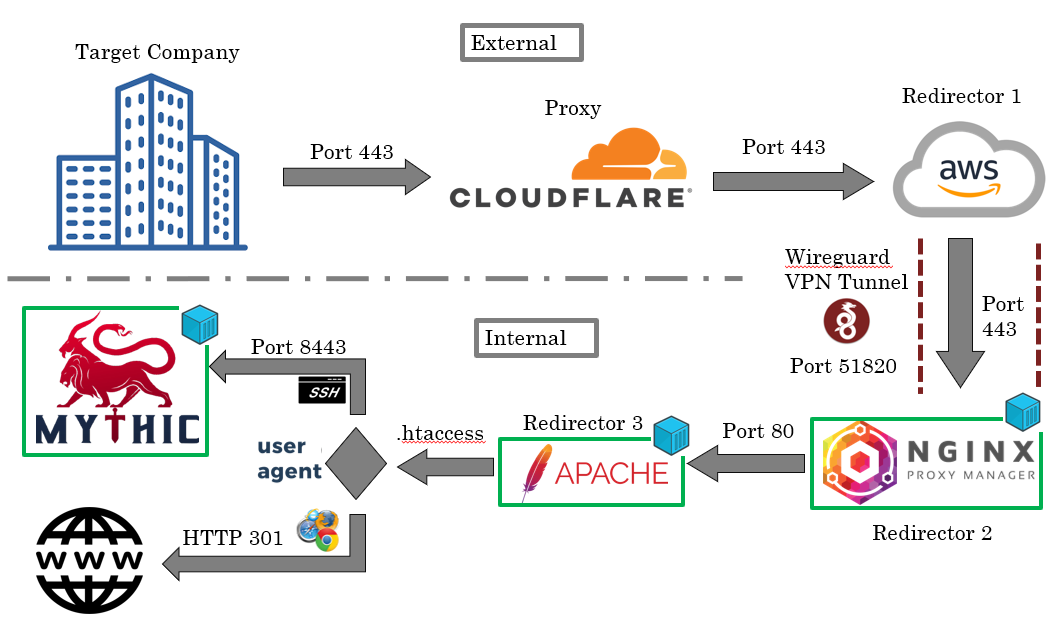
When it comes to penetration testing, red-teaming, or even malicious campaigns, Command and Control (C2) infrastructures play a crucial role in maintaining stealthy communication between the operator and the target systems. Today, let’s unravel a C2 infrastructure setup, layer by layer, to understand how it works and why it's designed the way it is.
The image above showcases a typical C2 architecture, meticulously crafted to blend into legitimate traffic flows, obfuscate origins, and stay resilient against detection. Let's walk through each part of this setup and explore its functionality.
The Outer Shell: External Components
- Target Company This represents the environment or systems being engaged by the operator. It could be anything from a compromised machine to a legitimate endpoint communicating with the infrastructure. From the target’s perspective, the setup must look benign and trustworthy—an essential goal of this C2 design.
- Cloudflare as the First Line of Defense The first stop for traffic is Cloudflare, a popular Content Delivery Network (CDN) and web proxy service. Here’s why it’s a vital part of the infrastructure:IP Masking: Cloudflare hides the real IP address of the infrastructure, making it harder to trace back to the C2 server. Traffic Encryption: Using Port 443 (HTTPS), it encrypts traffic to avoid triggering network alarms. Legitimacy: Cloudflare traffic blends in with legitimate internet communication, making detection by automated systems more challenging.
- AWS Redirector Once the traffic passes through Cloudflare, it’s routed to a redirector hosted on AWS, which acts as another layer of obfuscation. This redirector:Listens on Port 443 (standard HTTPS). Forwards the incoming traffic to the internal infrastructure via a WireGuard VPN tunnel. This secure tunnel ensures that even if the redirector is analyzed, the next hop remains hidden. The Inner Workings: Internal Components After traveling through the external maze, the traffic enters the inner infrastructure—where the actual magic happens.
- WireGuard VPN Tunnel A secure WireGuard VPN acts as the bridge between the external AWS redirector and the internal components. This encrypted tunnel ensures confidentiality and prevents attackers (or defenders) from inspecting the traffic at this stage.
- Nginx Proxy Manager (Redirector 2) The first stop inside the internal network is the Nginx Proxy Manager, which operates on Port 80. This reverse proxy serves as a middleman, forwarding incoming requests to the next stage based on specific rules. It’s highly customizable, making it ideal for filtering traffic or performing basic load balancing.
- Apache (Redirector 3) Next, we have an Apache web server, which further scrutinizes the incoming traffic. This redirector:Uses an .htaccess file to define rules, such as restricting access based on user agent strings. For example, only requests from a legitimate implant or operator might be allowed, while others are blocked. Handles valid requests by forwarding them to the final destination—Mythic, the C2 framework.
- Mythic: The Brain of the Operation At the heart of this infrastructure is Mythic, an open-source C2 framework beloved by red-teamers. It operates on Port 8443, offering:Operator Control: A dashboard for issuing commands, retrieving data, and controlling implants. Encrypted Communication: Ensures that all traffic between Mythic and its implants remains secure. Mythic is where the operator interacts with the compromised targets. However, thanks to the layers of redirectors, its actual location is heavily concealed.
Why So Many Layers?
This intricate setup might seem over-engineered at first glance, but every layer serves a distinct purpose:
- Obfuscation: Each hop (Cloudflare, AWS, VPN) masks the true location of the C2 server, making it nearly impossible to trace.
- Resilience: If one redirector is discovered and shut down, the rest of the infrastructure remains intact.\
- Legitimacy: By routing traffic through trusted services like Cloudflare and AWS, the operator blends in with normal internet activity.
- A Final Touch: HTTP 301 Redirects. Notice the mention of an HTTP 301 in the diagram? This likely indicates that redirections are being used to manage traffic flow. For example:
- Requests from unauthorized sources could be redirected elsewhere, or dropped entirely.
- Legitimate requests are funneled into the infrastructure, following the predefined paths.
Conclusion
This C2 infrastructure is a masterclass in stealth and obfuscation, showcasing the level of sophistication red-teamers and adversaries alike bring to their operations. From Cloudflare masking the real IP to Mythic serving as the command hub, each piece fits perfectly into a puzzle designed to avoid detection.
By understanding these setups, defenders can better anticipate how attackers operate and design strategies to unmask and disrupt such infrastructures.